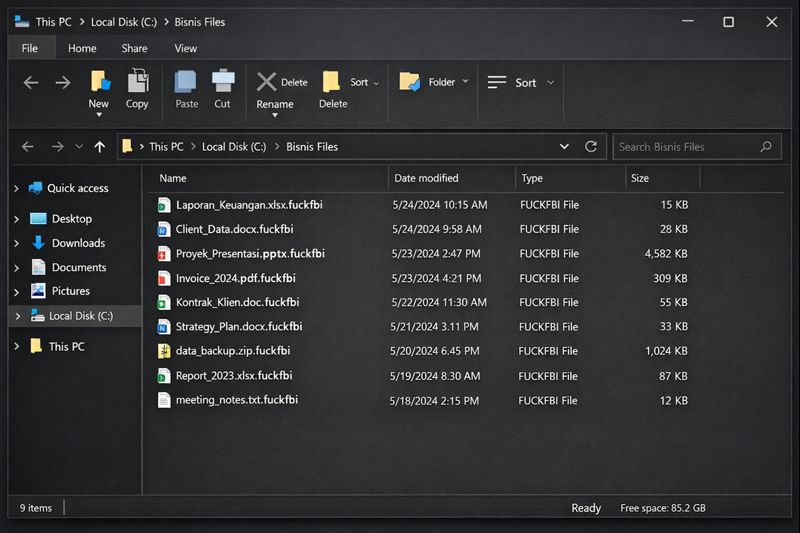
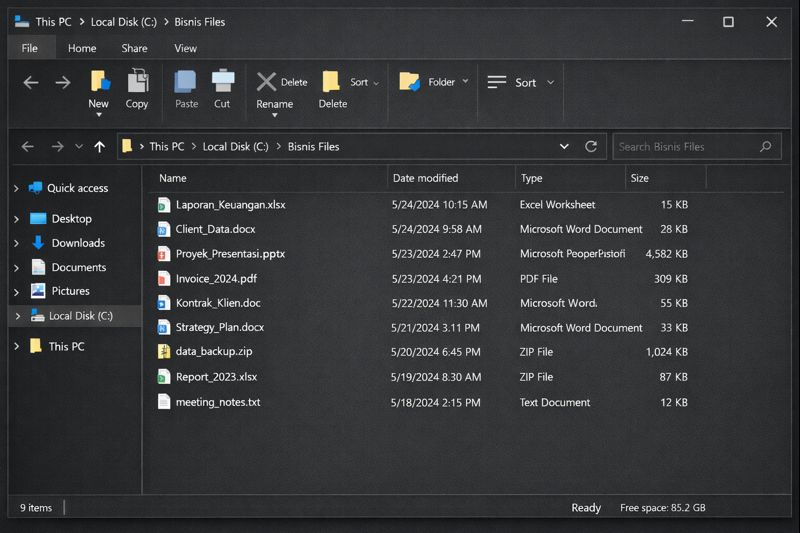
The first sign of trouble in this American firm was subtle. Staff reported that documents on the shared drive would not open, and some project folders suddenly “disappeared” from normal view. When the IT team checked the main file server, they saw that critical business documents had been renamed with the .fuckfbi extension, and a ransom note called READ_ME_FBI.txt was sitting at the root of multiple shared folders. It was clear: FuckFBI Ransomware had locked shared business files and the company faced a serious incident.
From that moment, the difference between months of chaos and a controlled recovery depended on the next steps.
How FuckFBI Ransomware Locked Shared Business Files
The attack focused on the file server that staff used every day:
- Shared departmental folders for finance, sales, operations, and legal.
- Central repositories for templates, contracts, and internal policies.
- Export locations for ERP, CRM, and reporting tools.
Applications still ran, email still worked, but the documents that made those processes meaningful were inaccessible. Without those shared files, teams could not finalize proposals, issue invoices, or review contracts. The business risk was immediate and very real.
Containment Steps for FuckFBI Ransomware in a US Firm
Instead of guessing or experimenting with random tools, the IT team focused on containment.
They quickly:
- Disconnected the affected file server and backup targets from the network.
- Disabled non-essential remote access and stale admin accounts.
- Warned staff not to open suspicious files, not to rename encrypted documents, and not to download “free decryptors.”
- Collected a small set of encrypted documents and system logs for later analysis.
This stopped FuckFBI Ransomware from reaching other servers and endpoints that were still clean. It also preserved the environment in a state that could be understood and used for recovery planning.
Explaining Impact to Management Without Jargon
Next, IT and operations prepared a short briefing for management in plain language.
They answered three things:
- What is broken: shared business files on the main file server; many documents staff rely on every day.
- What still works: email, some cloud apps, and line-of-business systems that do not depend directly on the locked shares.
- What is at risk: revenue, project timelines, contract processing, audits, and overall credibility if the company cannot respond quickly.
This framing helped leadership see that this was a serious FuckFBI Ransomware event but not a total collapse. They agreed to support a structured recovery effort rather than push for a rushed ransom payment.
Technical Assessment and Specialist Support
With containment and executive backing in place, the team moved into structured assessment.
They mapped:
- Which shares and folders were affected versus which remained untouched.
- How those shared folders were used by applications and workflows.
- Which backups existed, where they lived, and whether any were offline or offsite.
After collecting encrypted samples and logs, the firm contacted ransomware recovery specialists via FixRansomware.com and submitted sample files securely through app.FixRansomware.com. The goals were to confirm the exact ransomware behaviour, avoid destructive guesswork, and design a realistic recovery plan.
For overall guidance, the team also referred to the official CISA Ransomware Guide (CISA/MS-ISAC Ransomware Guide), which emphasises isolation, structured analysis, and restoration from trusted backups instead of blindly negotiating with attackers.
Restoring Access to Shared Files After FuckFBI Ransomware
Once they had a full picture, the company and specialists designed a recovery plan focussed on business impact, not just file counts.
Key parts of the plan:
- Clone affected volumes before testing
The file server disks were cloned at the sector level. All experiments and potential decryption efforts were performed on the clones, keeping original disks intact as a safety net. - Identify clean, trustworthy backups
Backups taken before the infection window were located and validated in an isolated environment. These backups became the base for restoring critical shared folders. - Restore by business priority
Shared folders for finance, sales, and ongoing projects were restored first, followed by legal and archival data. Low-priority content was scheduled for later phases. - Rebuild recent changes where backups were incomplete
Where some very recent edits were missing from backups, the team reconstructed them from email attachments, local copies on user laptops, and exports from unaffected systems. Every manual reconstruction was documented and verified by data owners. - Validate and then reopen access gradually
Before unlocking the new shares for everyone, key users tested common workflows: generating invoices, drafting contracts, preparing reports. Only when these tasks succeeded reliably did the team allow wider access.
Lessons from a FuckFBI Ransomware Case in the US
In the end, the American firm restored access to shared business files without paying ransom. The FuckFBI Ransomware incident delivered several practical lessons:
- Shared file servers are critical infrastructure and must have layered, regularly tested backups, including at least one offline or immutable copy.
- Remote access and privileged accounts must be tightly controlled, logged, and reviewed.
- A simple, written incident response playbook for ransomware on shared drives can significantly reduce confusion and downtime.
This case showed how quickly FuckFBI Ransomware can lock shared business files in an American firm—but it also proved that disciplined containment, clear communication, and expert-led recovery can bring access back safely and leave the organisation stronger than before.