It started as a routine workday in a company in Timor-Leste. Staff complained that critical applications froze, logins took too long, and shared folders timed out. When the IT team checked key servers, they saw that important data files had been renamed with a new extension .hels, and a single ransom note file called hels.readme.txt appeared in several core directories. At that point, there was no doubt: BLACK-HEOLAS Ransomware had locked key systems and put the business at serious risk.
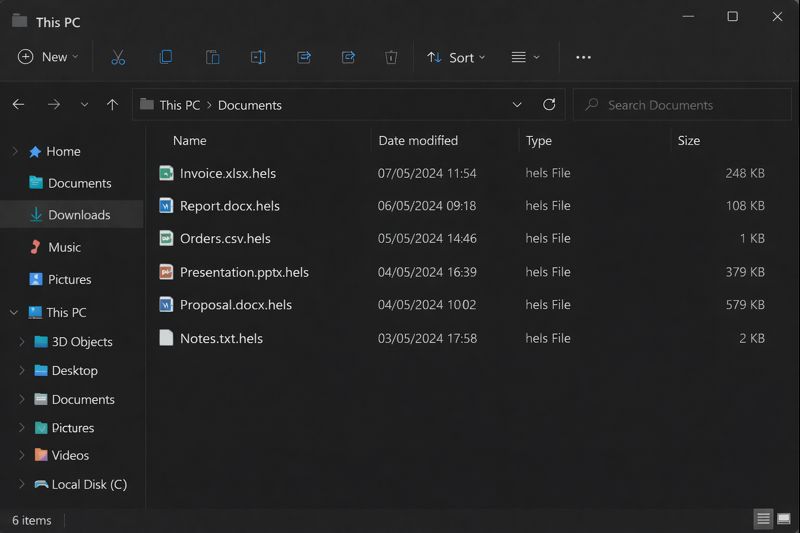
From that moment, the difference between total chaos and a controlled recovery depended on what happened in the next few hours.
How BLACK-HEOLAS Ransomware Affected Key Systems
The ransomware did not just touch one isolated server. It impacted several layers of the environment in Timor-Leste:
- Application servers that supported daily operations could not access their data.
- File shares used for documents, reports, and exports became unreliable or unreadable.
- Some scheduled jobs failed silently, causing gaps in data and missing outputs.
Users still had email and some cloud tools, but the systems that actually ran the business were locked. That meant lost productivity, delayed decisions, and pressure from customers waiting for responses.
Immediate Containment Instead of Panic
The first technical step was containment. Trying random tools or rebooting everything would only make the situation worse.
The IT team:
- Disconnected affected servers and storage from the network to stop further spread.
- Disabled unnecessary remote access (RDP, VPN accounts that were not essential).
- Instructed staff not to open suspicious files or download “free decryptors” from the internet.
- Collected a small set of encrypted samples and system logs for later analysis.
This stopped BLACK-HEOLAS Ransomware from jumping into additional servers or reaching backup devices that were still clean. It also preserved the environment in a state that could be studied and used for recovery planning.
Explaining the Situation to Management in Simple Terms
Next, the technical team had to translate the incident into business language. Management needed a clear picture, not a flood of jargon.
The explanation focused on three questions:
- What is down right now? Some core applications, shared data, and operational reporting.
- What still works? Email, some external services, and basic communication channels.
- What is at risk? Service delays, missed deadlines, potential financial impact, and reputational damage if the incident is not handled properly.
With this clarity, leadership in Timor-Leste accepted that this was a BLACK-HEOLAS Ransomware crisis and agreed to support a structured recovery plan instead of pushing for rushed, risky actions.
Technical Assessment and Specialist Involvement
After containment and alignment with management, the team moved into technical assessment.
They mapped:
- Which servers, applications, and shares were encrypted.
- Which parts of the infrastructure still held clean copies of data.
- How backups were configured and where offline or offsite copies might exist.
Encrypted samples and relevant logs were reviewed. The company then contacted ransomware recovery specialists through FixRansomware.com and uploaded samples via the secure portal app.FixRansomware.com. The objective was to confirm the exact BLACK-HEOLAS Ransomware behaviour and identify realistic recovery options.
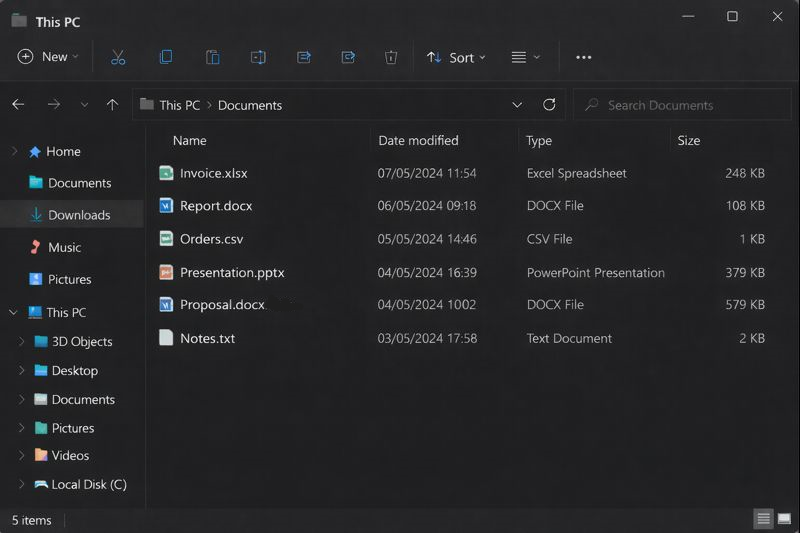
To guide overall strategy, the team also referred to the official CISA Ransomware Guide (CISA/MS-ISAC Ransomware Guide), which emphasises isolation, structured analysis, and restoration from safe sources.
Recovery Plan: Bringing Key Systems Back Online
With more information in hand, a recovery plan tailored to the environment in Timor-Leste was built.
Key elements:
- Clone before touching production disks
Affected volumes were cloned at the disk level. All tests and any possible decryption attempts were performed on these clones, leaving original disks intact in case a different approach was needed later. - Identify clean backups and surviving data sources
Backup sets stored on separate media and offsite locations were reviewed. Clean copies from before the incident became the baseline to restore key applications and shared data. - Restore in business-first order
Systems that directly affected customers, revenue, and core operations were restored first. Less critical archives and older data sets were scheduled for later phases. - Rebuild the last portion of data where necessary
For recent periods not fully covered by backups, data was reconstructed using email exports, external system logs, and files preserved on endpoints that were not encrypted. Each manual adjustment was documented for audit and quality control. - Validate before opening access
Key users from operations, finance, and management tested restored systems. Only when core functions behaved as expected were more users allowed back into the environment.
Lessons Learned from the BLACK-HEOLAS Ransomware Case
In the end, the company in Timor-Leste brought key systems back online without paying ransom. The BLACK-HEOLAS Ransomware attack highlighted several critical points:
- Backups must include at least one offline or immutable layer, especially for core application data.
- Remote access and privileged accounts require strict control, monitoring, and regular review.
- A documented, tested incident response plan can turn a full-blown crisis into a manageable project.
The incident proved how fast BLACK-HEOLAS Ransomware can lock key systems. It also showed that disciplined containment, clear communication, careful technical assessment, and expert guidance can restore operations and leave the organisation stronger than before.

![Serviço de descriptografia do BLACK-HEOLAS ransomware [.hels] Timor-Leste.](https://fixransomware.com/wp-content/uploads/2025/12/MKP-ransomware-300x300.png)
