When staff at several public offices in North Carolina started their day, the first signs of trouble looked like “just IT being slow.” Case-management systems stalled, internal web portals timed out, and some desktops suddenly showed a new, ominous wallpaper. On closer inspection, the IT team discovered that key data files had been renamed with a new extension .NotHr, and a ransom note called NotHr-Attention.txt appeared in critical directories and on user desktops. At that point it was clear: NotHere Ransomware had disrupted public services and was actively attacking core systems.
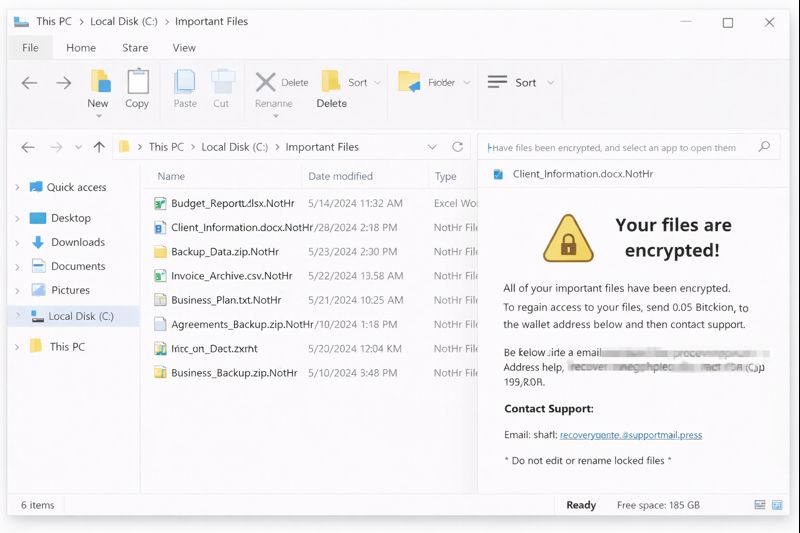
From that moment, what happened in the next 24 hours determined whether the incident would become a long-term crisis or a controlled recovery story.
How NotHere Ransomware Disrupted Public Services in North Carolina
NotHere Ransomware did not shut down the entire state at once. Instead, it targeted the data and systems that keep public services running day-to-day:
- Shared drives that stored citizen records, reports, and operational documents.
- Application servers for scheduling, case processing, and internal portals.
- Workstations in offices that interact directly with the public.
As a result, some departments in North Carolina had to switch to manual processes, slow walk-in service, and temporary “paper mode.” The network still technically worked, but citizens experienced delays, confusion, and partial outages.
First 24 Hours: Containment Before “Fixing” Anything
In the first 24 hours, the most important goal was containment, not instant repair.
The response team:
- Isolated affected servers and workstations from the network.
- Disabled non-essential remote access (VPN, RDP) and old privileged accounts.
- Instructed staff not to open suspicious files, not to rename encrypted documents, and not to install “quick-fix” tools from the internet.
- Captured logs, a small set of encrypted samples, the NotHr-Attention.txt notes, and screenshots of the changed wallpaper as evidence.
Because these steps were taken early, NotHere Ransomware could not spread further into still-clean systems, including backup repositories and secondary sites. The environment remained damaged, but stable enough to analyze and recover.
Explaining the Incident to Leadership and the Public
Next, IT and emergency management leaders needed a clear story for decision-makers and, eventually, citizens.
They focused on three points:
- What is impacted: specific public services facing slowdowns or partial outages, and which data areas are encrypted.
- What still works: phone lines, many cloud-based tools, and core systems that remain unaffected.
- What is at stake: continuity of essential services, public trust, and legal obligations for records retention and privacy.
This framing helped leaders understand that NotHere Ransomware was serious but manageable. It also allowed communications teams to craft honest updates to the public without causing unnecessary panic.
Technical Assessment and Specialist Support
With containment in place and leadership aligned, the technical team moved into a structured assessment phase.
They mapped:
- Which servers, shared folders, and applications were encrypted by NotHere Ransomware.
- Where authoritative data truly lived (databases, replicated systems, archives, and paper records).
- What backup strategies were in place, including any offline or offsite copies unaffected by the attack.
After collecting enough samples and logs, the organization brought in external ransomware-recovery specialists via FixRansomware.com and securely uploaded representative encrypted files through app.FixRansomware.com. The aim was to confirm the NotHere Ransomware behavior, evaluate realistic recovery paths, and avoid destructive trial-and-error.
For overarching guidance, the team followed the CISA StopRansomware Ransomware Guide which emphasizes isolating systems, analyzing impact, and restoring from trusted backups instead of rushing to pay ransom.
Restoring Critical Data and Public Services
Once they understood the scope, the North Carolina public organization and its partners designed a business-first recovery plan.
Key steps included:
- Cloning affected disks
Before attempting any changes, the team created full disk clones of affected servers. All tests and potential decryption attempts happened on clones, preserving original evidence and data as a last-resort fallback. - Validating clean backups
Backups taken before the NotHere Ransomware intrusion window were restored into an isolated environment. After verifying integrity, these backups became the starting point for restoring key applications and shared data. - Restoring by service priority
Systems supporting essential public services—such as case processing, scheduling, and critical reporting—were prioritized. Less critical archives were scheduled for later. - Reconstructing gaps where backups were incomplete
For time periods not fully covered by backups, teams used email attachments, partner systems, paper records, and unencrypted copies on endpoints to rebuild missing information. Every reconstruction was documented and reviewed by data owners. - Testing end-to-end workflows before reopening access
Before staff resumed normal operations, key procedures—like opening a case, updating a record, and generating required reports—were tested end-to-end. Only after successful tests did the organization gradually restore full access.
Lessons from a NotHere Ransomware Case in North Carolina
In the end, the public organization restored critical data and services without paying ransom. This NotHere Ransomware incident highlighted several important lessons:
- Public service networks must treat shared data and application servers as critical infrastructure, with layered, tested backups that include at least one offline or immutable copy.
- Remote access and privileged accounts require strong controls, regular audits, and multifactor authentication wherever possible.
- A simple, written incident response playbook for ransomware, shared across IT, leadership, and communications, significantly reduces confusion and downtime.
This North Carolina case shows how NotHere Ransomware can disrupt public services—but it also proves that disciplined containment, clear communication, and expert-guided recovery through FixRansomware.com can restore critical data safely and strengthen resilience for the future.


