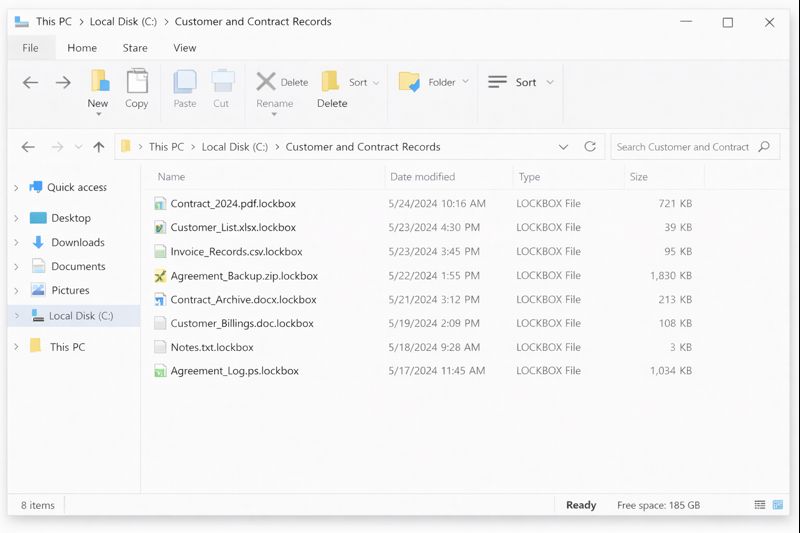
The incident in this Dutch company started with “small” complaints: the CRM felt slow, some contract folders would not open, and shared drives returned random errors. When the IT team checked the core file server, they saw that many customer and contract documents had been renamed with a new .lockbox extension, and a ransom note called README.txt sat in important directories. It was clear that Rusty Lockbox Ransomware was actively damaging customer and contract records.
From that moment, the choice was simple: either panic and make it worse, or follow a structured recovery path.
How Rusty Lockbox Ransomware Hit Customer and Contract Records
Rusty Lockbox did not immediately take down all systems. Email and some SaaS tools still worked. The real impact was on the data layer:
- Customer folders and CRM export files became unreadable.
- Contract archives and legal documents could not be opened or searched.
- Reporting jobs that relied on these files started failing silently.
In practice, sales and legal teams in the Dutch company lost visibility on customers, terms, and obligations. That meant delays in deals, slower renewals, and risk around compliance and disputes.
Containment First: Stop the Spread
The IT team resisted the urge to “try tools” from the internet. They focused on containment:
- The affected file server and any directly attached storage were disconnected from the network.
- Non-essential remote access paths and old admin accounts were disabled.
- Staff were told not to open suspicious files or rename encrypted ones, and not to download “free decryptors.”
- Logs and a small set of encrypted samples were preserved for later analysis.
This stopped Rusty Lockbox Ransomware from moving further into other servers, endpoints, and backup repositories that were still clean. It also kept the environment stable enough for a controlled recovery.
Explaining the Situation to Management in Plain Business Terms
Next, IT and operations prepared a short, non-technical briefing for management:
- What is affected: customer records, contract documents, and some related reporting files.
- What still works: email, certain cloud platforms, and systems not tied directly to the damaged data.
- What is at risk: revenue, contract renewals, audit readiness, and client trust if recovery is slow or mishandled.
With this clarity, leadership understood that this was a serious Rusty Lockbox Ransomware incident but not the end of the company. They agreed to support a structured recovery plan and avoid an emotional rush toward paying ransom.
Technical Assessment and Bringing in Specialists
With containment and management alignment in place, the team began a structured technical assessment:
- Mapping which shares and directories held encrypted customer and contract records.
- Identifying where original data lived: databases, document management systems, and external partners’ portals.
- Reviewing backup setups: on-premise, cloud, and any offline or offsite copies.
Encrypted samples and relevant logs were then shared securely with specialist responders via FixRansomware.com and app.FixRansomware.com. The goals were to confirm the Rusty Lockbox family, understand realistic recovery options, and avoid destructive guesswork.
For overall strategy, the team also followed guidance from the official CISA StopRansomware Ransomware Guide, which emphasises isolating affected systems, performing structured analysis, and restoring from trusted sources.
Recovery: Getting Customer and Contract Data Back Safely
Once they had a clear picture, the Dutch company and external experts designed a business-focused recovery plan:
- Clone before touching production
Disk-level clones of affected volumes were created. All tests and any potential decryption attempts were run on clones, keeping original disks untouched. - Validate clean backups
Backups taken before the infection window were restored into an isolated environment and checked for integrity. Clean restore points became the base for customer and contract data. - Restore by business priority
Active customer records, ongoing contracts, and documents needed for current negotiations and audits were restored first. Historical archives and low-priority files were scheduled for later phases. - Rebuild recent gaps
Where backups did not cover the most recent changes, data was reconstructed using email attachments, CRM exports, and files still present on unaffected endpoints. All manual reconstructions were documented and confirmed by business owners. - Test end-to-end workflows
Sales, legal, and finance teams tested key workflows: viewing customer history, checking contract terms, and preparing documentation for clients. Only when these workflows ran reliably did the company reopen general access to the restored data.
Lessons from the Rusty Lockbox Ransomware Case in the Netherlands
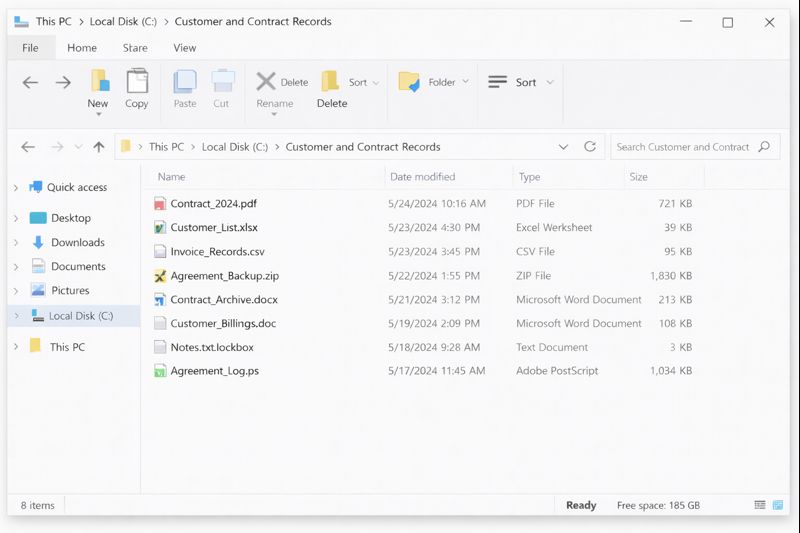
The Dutch company successfully recovered critical customer and contract records without paying ransom. The Rusty Lockbox Ransomware incident left several clear lessons:
- Customer and contract data must be treated as critical assets with layered, tested backups, including at least one offline or immutable layer.
- Access control and remote entry points to file servers need strong governance and regular reviews.
- A written, simple incident response playbook that includes ransomware on shared data is essential for any organisation that depends on documents and contracts.
This case shows how quickly Rusty Lockbox Ransomware can damage customer and contract records in a Dutch company, and also how disciplined containment, clear communication, and expert-guided recovery through FixRansomware.com can bring data back safely and leave the organisation more resilient than before.


