Why have my VMware virtualization and Veeam database server backups had their file extensions changed to .Qilin/.Agenda and can no longer be opened?
Are you wondering why your files have been renamed with a .Qilin or .Agenda extension and can no longer be opened? That is a sign that you have been hit by the Qilin/Agenda ransomware.
The Qilin/Agenda ransomware is malware that locks access to your files by encrypting them. When this happens, the hackers rename the encrypted files. For example, a file named “1.SQL” might become “1.SQL.Qilin”, and “FILE_PENTING.VMDK” would become “FILE_PENTING.VMDK.Qilin”.
Additionally, attackers often assign a unique ID to each victim. This ID is the hackers’ way of marking which server or company has been attacked, helping them to track their victims. If multiple servers are infected, each may be assigned its own unique encryption ID.
Fortunately, fixransomware.com has successfully recovered server data for companies in Malaysia and Indonesia that were seeking decryption services in Jakarta—the recovery was fast, affordable, and 100% successful, as shown in the following “Successful .Qilin/Agenda Decryption: Before & After” image:
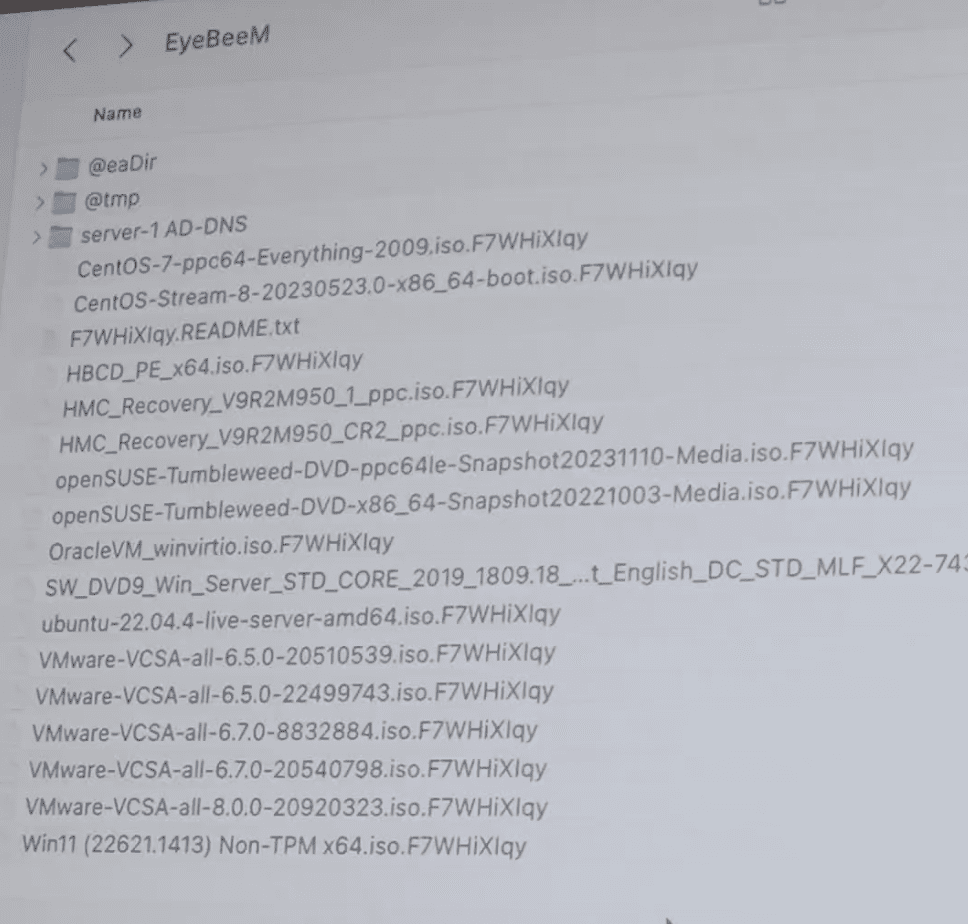
Modern ransomware like .Qilin/Agenda doesn’t just target active files; it also aggressively hunts for backup copies. According to an analysis from the Sophos Threat Lab 2025, this ransomware uses PowerShell & RDP-based lateral movement techniques to find and encrypt NAS backups, even those that are only active intermittently.
This makes even the 3-2-1 backup strategy less effective without proper network segmentation and offline air-gaps. The ransomware is also known to deploy malware loaders like Emotet and Qakbot, which can remain dormant for up to 3 weeks before the final encryption is executed.
The public key is used to encrypt the symmetric encryption key (like AES) which in turn is used to encrypt the victim’s files, while the private key is required to decrypt those symmetric keys. To prevent the victim or a third party from using this private key, the ransomware encrypts the Cpriv.key using the attacker’s own public key (Spub.key).
The file resulting from this process is often saved with a name like “cpriv.Qilin” or “cpriv.Agenda” in the root directory of each drive and in specific user directories.
The .Qilin/Agenda ransom note will look like this, typically found in a file named +README-WARNING+.txt:
— Agenda
Your network/system was encrypted.
Encrypted files have new extension.
— Compromising and sensitive data
We have downloaded compromising and sensitive data from you system/network
If you refuse to communicate with us and we do not come to an agreementyour data will be published.
Data includes:
– Employees personal dataCVsDLSSN.
– Complete network map including credentials for local and remote services.
– Financial information including clients databillsbudgetsannual reportsbank statements.
– Complete datagrams/schemas/drawings for manufacturing in solidworks format
– And more…
— Warning
1) If you modify files – our decrypt software won’t able to recover data
2) If you use third party software – you can damage/modify files (see item 1)
3) You need cipher key / our decrypt software to restore you files.
4) The police or authorities will not be able to help you get the cipher key. We encourage you to consider your decisions.
— Recovery
1) Download tor browser: hxxps://www.torproject.org/download/
2) Go to domain
3) Enter credentials
— Credentials
Extension: –
Domain:
login: –
password: -(EXTRA string=same as login)
Can my data be recovered by paying the hacker or by downloading a free .Qilin/Agenda ransomware decryptor from sources like Emsisoft/Avast?
Many victims of the .Qilin/Agenda ransomware are tempted to pay the ransom, lured by the promise of file recovery. However, a study from Cybersecurity Ventures states that only 28% of victims who pay actually get all their data back, while the rest often experience repeated extortion (double extortion). Using pirated tools from sites like Kuyhaa is extremely risky as they often contain new malware that provides access for a second-stage attack.
The use of third-party decryptors from sources like Emsisoft or Avast to unlock or recover data can potentially damage your files, as has been reported in major ransomware discussion groups. Moreover, paying the ransom offers no guarantee of data recovery, as hackers are solely seeking profit by selling stolen data on the dark web or demanding more money for political aims.
Furthermore, paying the ransom increases the risk of your company being targeted again, placing your privacy and security in further jeopardy. Therefore, if you are hit by a ransomware attack, contact the fixransomware.com team immediately. We offer a .Qilin/Agenda decryptor solution to decrypt servers running MSSQL, MYSQL, and even Accurate databases affected by ransomware, providing an effective way to overcome the virus.

How can the .Qilin/Agenda ransomware virus attack your network? And how do you clean it?
A. Entry Methods of .Qilin/Agenda Ransomware and Vulnerability Statistics Exploited by the Makop Virus! (Dissection):
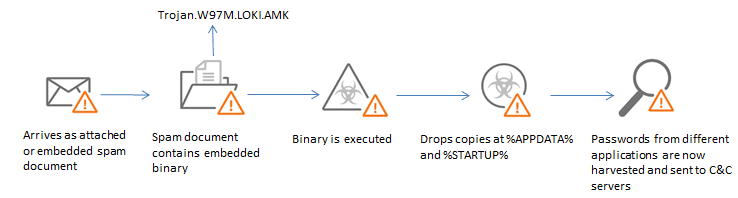
If you are asking why my data’s file extension has changed to .Qilin/Agenda and cannot be opened, it can be caused by the various ways this ransomware spreads. When the malware is active, it executes three critical stages: (1) Reconnaissance of backup patterns, (2) Layered encryption—a unique AES key per-file which is then wrapped with an RSA public key, and (3) Deletion of shadow copies to make automatic Windows recovery fail. As a result, your file—for example, DB.mdf—is changed to DB.mdf.[ID].Qilin/Agenda and cannot be opened. The Kaspersky Q1-2025 report shows a 41% increase in ransomware attacks targeting SAP HANA and domain controller databases. Its variants are often spread via the Qakbot loader or Fortinet/Cisco VPN zero-day exploits.
Additionally, in terms of tactics and techniques, .Qilin/Agenda uses various methods to gain initial access to a victim’s network, including:
- Valid Accounts (T1078): The threat actors use brute-force techniques to guess RDP service passwords. If the guessed password belongs to a domain administrator, they can execute commands with higher privileges.
- Phishing (T1566): In some cases, the ransomware is delivered via phishing emails as an attachment.
- External Remote Services (T1133): The threat actors exploit vulnerable RDP services on the victim’s network to gain initial access.
After gaining access, .Qilin/Agenda executes a batch script that calls a PowerShell script to spread the ransomware throughout the network. This ransomware also uses the Windows Management Instrumentation command-line utility (wmic) to delete volume shadow copies, preventing victims from recovering the encrypted data.
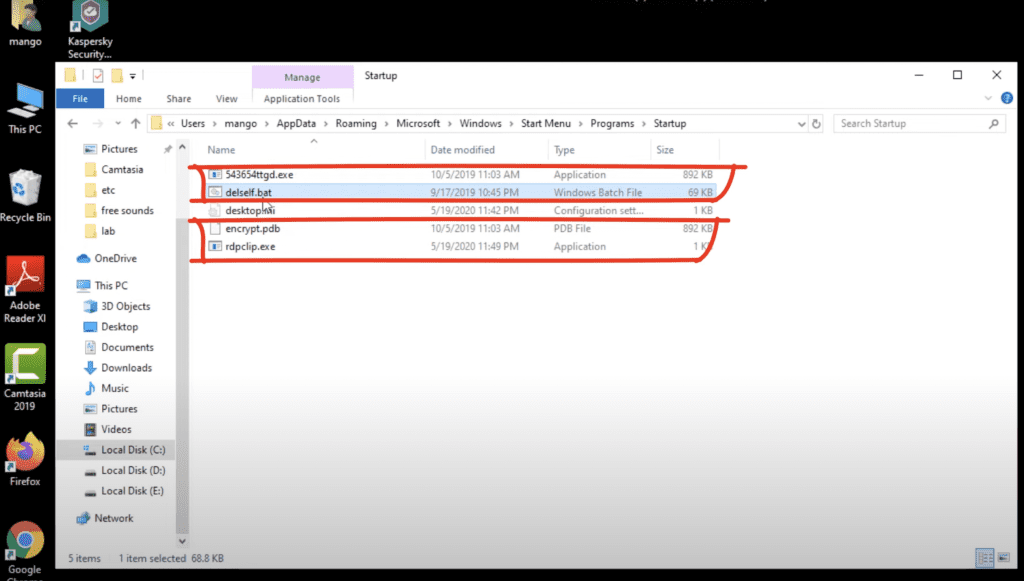
To maintain persistence, .Qilin/Agenda adds a registry entry to ensure the ransomware is executed at system startup. Additionally, this ransomware creates a scheduled task named “svhost” that automatically runs the ransomware every 15 minutes.
In an effort to avoid detection, .Qilin/Agenda disables security products like antivirus and boots the system into safe mode, where the Windows operating system starts with a limited set of drivers and services, thereby bypassing endpoint defenses.
To escalate privileges, .Qilin/Agenda uses a built-in Windows tool called Microsoft Connection Manager Profile Installer (cmstp.exe) to bypass User Account Control (UAC) and execute commands with higher privileges.
In terms of impact, .Qilin/Agenda uses a hybrid encryption approach. The victim’s files are encrypted with the AES-256 symmetric encryption algorithm, and the secret key is encrypted with RSA-2048 public-key encryption. This ransomware also deletes backup copies of the encrypted files to prevent victims from recovering them. Therefore, contact the Fixransomware.com Technician team to protect yourself from subsequent attacks:

B. Characteristics of the .Qilin/Agenda Ransomware, Hacker Email Identities, & Some Facts About the Technology Used (Technical Analysis):
If you are asking why my data’s file extension has changed to .Qilin/Agenda and cannot be opened, the characteristics and technical analysis of the MKP ransomware indicate that this ransomware uses the EMAIL instant messaging protocol for communication. This ransomware has the ability to avoid encryption on folders containing the words “Windows” or “Winnt” as well as files with specific extensions like .exe and .dll. The Ziver ransomware uses AES256 for encryption, controls registry access for persistence, and uses system APIs to gather system information, manage processes, and manipulate files and memory.
Hybrid Encryption Method: As mentioned before, .Qilin/Agenda uses a combination of AES-256 symmetric encryption and RSA-2048 public-key encryption. Each file is encrypted with a unique AES key, and then that AES key is encrypted with RSA.
Specific File Exclusion: To avoid damaging the operating system, this ransomware ignores system folders like Windows or WinNT and does not encrypt files with certain extensions (e.g., *.exe, .dll). The goal is to allow the computer/server to still be able to boot and display the ransom note, and for the victim to be able to execute the extortion steps. Additionally, the ransomware often stores its configuration in the Registry and adds a Run entry for persistence (to automatically run again upon restart).
Utilization of Windows Features: The perpetrators utilize living-off-the-land binaries. For example, .Qilin/Agenda is known to use the Windows utility CMSTP.exe (Connection Manager Profile Installer) to bypass User Account Control (UAC) and run its payload with admin privileges without being detected. This is a common trick used by modern malware for silent privilege escalation.
Spreading on the Network: After getting into one server, this ransomware can spread via SMB or scripts that push the executable to other machines (for example, via GPO if the Domain Controller has been compromised). The attacker often automates the spreading with scheduled tasks. In the case of .Qilin/Agenda, a malicious scheduled task named “svhost” was found, set to run every 15 minutes to keep the ransomware active on the system even if it is stopped.
Anti-Detection: .Qilin/Agenda also executes anti-forensic and anti-detection steps. It will attempt to turn off security services (utilizing the net stop command or Registry tweaks to disable real-time protection). Some strains even create a firewall rule to block connections to antivirus update domains, preventing the antivirus from updating its definitions. By running the encryption in Safe Mode and shutting down security services, this ransomware attempts to avoid detection by endpoint security.
A Decryption / Recovery Solution for Data Encrypted by the .Qilin/Agenda Virus: 100% Recovery, Free, and Fast
One of the best solutions to unlock/decrypt the .Qilin/Agenda ransomware with an online ID is to manually use various techniques, such as asymmetric decryption [aka Public-Key Cryptography] (RSA, El Gamal, etc.), Key Exchange Algorithms (Diffie-Hellman), and the use of Shor’s algorithm via online Quantum Platforms like IBM-Q. Generally, you first need to perform a file-hash check for an initial analysis of the file’s health and the time required for decryption.
Various .Qilin/Agenda ransomware strains implement an advanced cryptographic scheme with a combination of the AES-256 symmetric encryption algorithm for individual files and RSA-2048 to encrypt those AES keys. In fact, the cpriv.Qilin/Agenda file, which contains the victim’s decryption private key, is also re-encrypted using the attacker’s public key (Spub.key). This makes manual decryption nearly impossible without access to quantum computing systems or the exploitation of a specific weakness in its encryption implementation.
A 2024 study from IBM X-Force states that the brute-force time for RSA-2048 with conventional devices would require over 300 trillion years. However, with the Variational Quantum Factoring (VQF) approach, that time can be shortened to less than 72 hours—a technique that has been adopted by Fixransomware.com.
Tutorial: How to Decrypt Data Attacked by Ransomware:
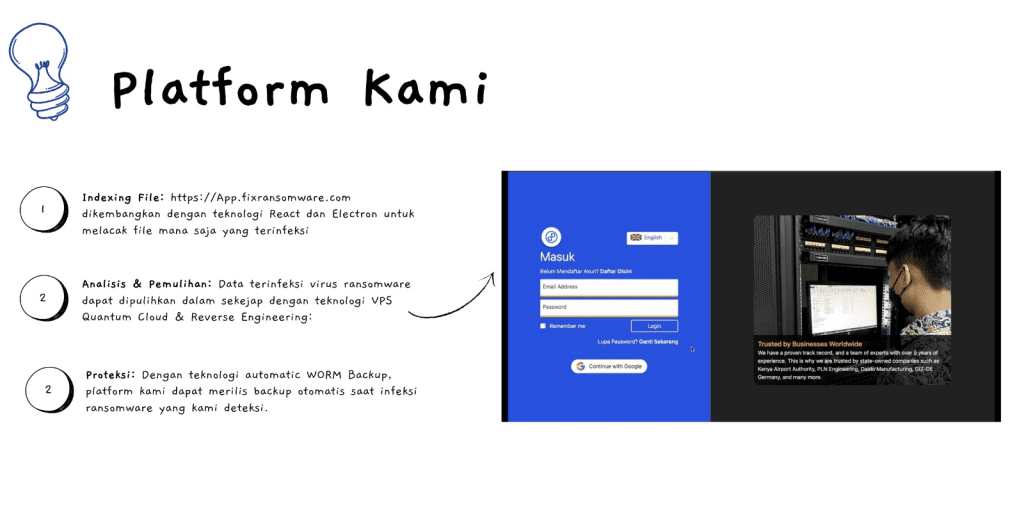
- Registration: First, click “Sign Up / Daftar” on the site http://app.fixransomware.com, fill out the form that appears, and click SIGN UP. You will receive a confirmation via email and WhatsApp. Be sure to click the “Confirm” button in the message to activate your account.
- Login and Scan: After the email confirmation, return to the site and log in using the email and password you registered. The next step is to click the “SCAN NOW” button and select the virus variant to begin the scanning process.
- Upload and Analysis: Upload the infected file (max 1MB) in the “Upload Sample & Terror Text” section and click “Analyze & Decrypt” after you agree to the provided terms. You just need to wait for the analysis results which will be sent via email, covering all details such as the data repair offer, estimated cost, timeline, and security recommendations.
- Recovery Process: After the quotation, invoice, and service agreement letter are completed, you can proceed to the decryption or recovery stage. The decryption progress will be continuously updated via email and WhatsApp.
Testimonial from a Client Whose Database Server and NAS were Infected by the .Qilin/Agenda Ransomware and Saved by the Fixransomware.com Application
One real case study comes from a Fixransomware client named Eko (a pseudonym), an IT manager at a national-scale public company. Their VMWARE ESXi 5.0 had never been patched and was vulnerable to CVE-2023-20867, a zero-day vulnerability that was exploited by Ziver to deploy the encryption binary. Manual recovery attempts instead resulted in the data being encrypted twice. After contacting Fixransomware, our team successfully restored the entire VMDK and VHD datastore within 2 business days, complete with hash validation and integrity checks.
How to Protect Yourself From Future Ransomware Attacks
Langkah 1: Pisahkan Segmentasi Jaringan Server/PC/Nas Terenkrip dengan Endpoint/PC.
Beberapa infeksi jenis ransomware dirancang untuk mengenkripsi file dan menyebar ke seluruh jaringan lokal. Untuk alasan ini, sangat penting untuk mengisolasi perangkat yang terinfeksi sesegera mungkin dengan cara pemisahan segmentasi kelas jaringan. Pemisahan segmen jaringan server dengan endpoint sangatlah krusial.
Endpoint device sangatlah rentan karena karyawan dengan mudah membuka file dan tautan yang diterima dari alamat hingga email yang tidak dikenal. Jika anda tidak yakin apakah sebuah situs bisa dipercaya atau tidak, maka konsultasikan dengan forum korban ransomware terbesar kami. Umumnya ransomware online ID dengan teknologi polymorphic dapat mengembed dirinya lewat dokumen pdf hingga gambar, sehingga penyebarannya kini tidak hanya lewat .exe.
Langkah 2: Cabut Seluruh Media Penyimpanan Eksternal, Logout Akun Cloud, dan Shadow Backup.
Seperti disebutkan di atas, ransomware umumnya melakukan survey jauh-jauh hari sebelum mengenkripsi data dan menyusup ke semua perangkat backup untuk menghapus data cadangan anda dan mencuri beberapa akun sosial media strategis. Untuk alasan ini, semua perangkat penyimpanan eksternal (flashdisk, harddisk Eksternal, NAS dll.).
Beberapa jenis ransomware dapat menginfeksi data yang disimpan di dalam “Cloud seperti Google Drive” ataupun NAS Synology/QNAP. Untuk alasan ini, Anda harus keluar dari semua akun vital atau mengganti sandi penyimpanan cloud di dalam browser dan perangkat lunak terkait lainnya. Anda juga harus mempertimbangkan untuk menghapus sementara perangkat lunak manajemen cloud sampai infeksi benar-benar hilang.
Langkah 3: Mematikan Virus di Windows Startup, Scheduler, Hosts, and Task manager
Selain itu, anda wajib untuk selalu mengupdate dan (atau) aktifkan Endpoint security yang didapatkan dari distributor resminya. Jika komputer Anda sudah terinfeksi ransomware .Qilin/Agenda, umumnya PC akan dibanjiri dengan malware yang membuat PC lambat saat dikoneksikan ke internet karena umumnya mereka sedang mengunduh data sensitif anda. Saat ini, pelaku ransomware tidak hanya mengenkripsi file, tetapi juga mencuri data korban untuk dipublikasikan jika tebusan tak dibayar. Beberapa grup bahkan menambahkan serangan DDoS (Distributed Denial-of-Service) sebagai metode tekanan tambahan (triple extortion). Laporan CISA 2024 menunjukkan peningkatan 60% kasus di mana data korban diunggah ke dark web setelah korban membayar tebusan sekalipun. sebaiknya jalankan pemindaian dengan antivirus Endpoint Fixransomware.com. Saat ini berlangsung flashsale diskon hingga 50% dari harga resmi serta demo gratis dari tim Bitdefender jakarta untuk 1 bulan.

Hampir seluruh jenis ransomware tipe online tidak dapat terdeteksi oleh antivirus biasa karena mereka dapat menyembunyikan kode jahat diri mereka dan mereplikasinya. Sehingga, jika Anda ingin menghidupkan Server/PC terinfeksi untuk tujuan analisis menggunakan platform kami (https://app.fixransomware.com), kami sarankan untuk mengakhiri proses tidak umum di task manager hingga folder startupun maupun file hosts disini. Dikarenakan keberhasilan fixransomware.com memecahkan semua varian ransomware, di beberapa kasus web kami Qilin/Agenda oleh peretas dengan memblacklist halaman kami di file hosts.
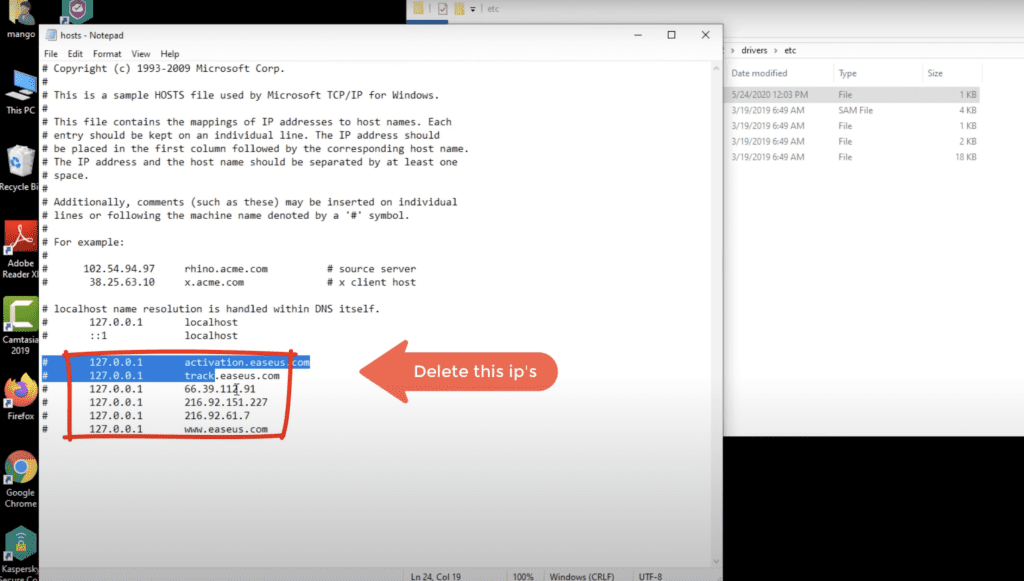
Jika Anda tidak ingin repot melakukanya secara manual, Anda juga dapat menghubungi CS https://fixransomware.com/ untuk mendapatkan Safe-mode Installer Sophos atau Bitdefender endpoint security untuk membersihkan semuanya. Digipedia juga memberikan suport remote anydesk untuk proses instalasinya secara gratis karena kami merupakan Gold partner Bitdefender dan Sophos.

Langkah 4: Membuat Backup Data dengan Metode 3-2-1 Baik Untuk Data Yang Sedang Terinfeksi dan Belum Terenkripsi.
Salah satu metode backup yang paling andal adalah dengan menggunakan perangkat penyimpanan eksternal dan tetap mencabutnya. Salin data Anda ke hard drive eksternal, flash didsk, SSD, HDD, atau perangkat penyimpanan lainnya, cabut dan simpan di tempat yang kering jauh dari matahari dan suhu ekstrim.
Namun, cara ini cukup tidak efisien, karena pencadangan dan pembaruan data perlu dilakukan secara berkala. Anda juga dapat menggunakan layanan cloud atau server jarak jauh. Di sini, koneksi internet diperlukan dan selalu ada kemungkinan pelanggaran keamanan, meskipun itu sangat jarang terjadi.


