01
Why Decryption and Analysis Services Incur Costs?
-
If a decryption or analysis package is beyond your budget, we offer alternative recovery methods or more affordable analysis options.
Some cases may seem costly because every new ransomware variant requires ongoing development of our decryption pattern database. This involves disassembling PE ransomware files each time a new strain emerges, demanding extensive technical expertise and resources.
Additionally, the highest operational cost comes from using IBM-Q Quantum Computing to run the Shor algorithm, with fees reaching $1.60 per second or starting at $96 per minute. You can verify this at:
🔗 IBM Quantum Pricing.
02
Can Ransomware Infect My Data Again in the Future? Can Antivirus Restore It?
Yes, ransomware can reinfect your system more than 4 times if proper prevention and backdoor removal measures are not implemented. Before recovering from a ransomware attack, it is crucial to ensure your system is fully cleaned of malware and security vulnerabilities are patched. Otherwise, the risk of reinfection remains. Some ransomware variants can even spread across networks, further increasing the chances of re-infection.
Antivirus software is designed to detect and remove malware, including ransomware. However, once ransomware encrypts your data, antivirus tools cannot decrypt or restore the encrypted files.
03
How much will it cost to recover my locked files?
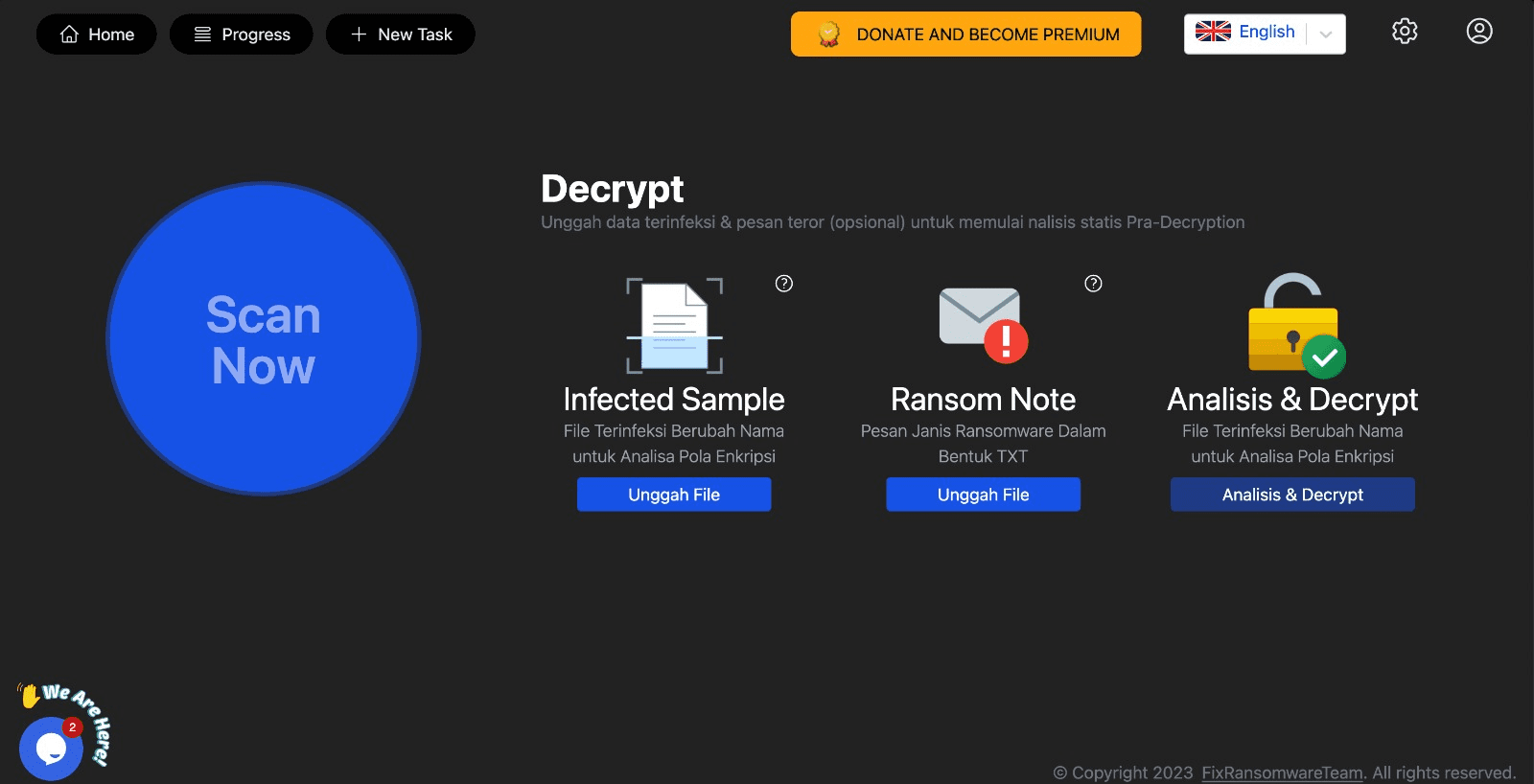
To estimate the cost of unlocking your encrypted files, please upload your infected files to https://app.fixransomware.com. Afterward, we will provide a static and dynamic analysis report detailing the timeline, cost, and sample recovery methods for similar cases. 
04
Can my lost files due to a ransomware attack be fully recovered 100%?
Fixransomware.com, Indonesia’s No.1 AES Decryption Company, Guarantees 100% Data Recovery
Fixransomware.com, the leading AES decryption company in Indonesia, can fully recover data encrypted by the latest online ID ransomware variants.
We offer multiple recovery methods, each with varying speed, success rates, and costs, which can be selected after an initial analysis.
As the only AES decryption expert company, we provide flexibility by helping you choose the best method through a Zoom consultation.
For assistance, contact us via our website or WhatsApp at +62 851-5778-7595.
05
Can Large/Complex Decrypted Data Be Used as Before?
At FixRansomware.com, we specialize in restoring encrypted data affected by ransomware, including but not limited to:
1. Virtual Disk Images: These files represent entire hard drives in a single or multiple file format. We use reverse engineering to decrypt ransomware-encrypted virtual disks and restore original data.
2. Database Files: We recover encrypted databases such as MDB (Microsoft Access) or GDB (InterBase) by analyzing their structure and format to ensure full restoration.
3. Complex Design Data: Our team can also restore encrypted design files from software like Revit, CAD, and 3D modeling applications.
4. Programming Files: Source code files encrypted by ransomware can be decrypted, including but not limited to languages such as Python, Java, and C++.
Recovering large or complex data requires in-depth analysis of ransomware behavior, including its encryption algorithm. Using reverse engineering, we analyze, decrypt, and restore files to their original state—ensuring they are fully functional as before.
06
Is There a 100% Data Recovery Guarantee & Refund?
At FixRansomware.com, we understand how valuable your data is, and we are committed to providing the best ransomware recovery service. That’s why we offer a 100% data recovery guarantee or a full refund:
✔ Data Recovery Guarantee: Our expert team is dedicated to retrieving your encrypted data. If, for any reason, we are unable to decrypt your files, we provide a 100% refund—this is our commitment to delivering trusted and reliable recovery services.
✔ Irrecoverable Corrupted Data: Unfortunately, if your files were already damaged before the ransomware attack, they cannot be repaired through decryption. Data integrity before infection is crucial for successful recovery.
✔ Reinfection by Another Ransomware: If your files get infected again by a different ransomware after the recovery process begins, we may not be able to restore them. We strongly advise taking preventive measures to secure your system from reinfection during recovery.
We prioritize the best data recovery solutions using advanced technology, experienced professionals, and a strong commitment to customer satisfaction. At FixRansomware.com, we ensure an effective, efficient, and reliable data recovery process.
07
I cannot see nearby Fixransomware office. Am I required to send the infected storage ?
You don’t need to send your HDD; static analysis can be performed directly on app.fixransomware.com. Dynamic analysis can be conducted either through on-site visits or remotely. Sending your hard drive to our office is only necessary if you’ve reached the decryption stage or if the decryption process is hindered by multiple VMs/hosts infected with different encryption variants. 
08
How Long The Ransomware Recovery Proccess Will Be?
Estimating the cost to recover files locked by ransomware like STOP/DJVU depends on several key factors:
• Data Header Damage Level: The more severe the damage from ransomware encryption, the higher the recovery cost.
• Ransomware Encryption Complexity: Ransomware types such as Elbie, Makop, Mallox, and Lockbit use advanced RSA AES encryption, requiring more resources for decryption.
• Type of Data to Be Recovered: Attacks on virtual machines and databases involve complex encryption, increasing recovery costs. In some cases, ransomware uses multiple encryption ID variants on different VMs, necessitating separate decryption processes for each VM/host.
Additionally, cost estimates are significantly influenced by the dollar exchange rate, as payment for IBM-Q quantum computer usage is required. The three variables above will determine which Cloud Quantum computer specifications will be used to reverse engineer ransomware with the Shor algorithm.
For a detailed analysis and cost estimate, please upload your infected files to our application at https://app.fixransomware.com. Afterward, we will provide a static or dynamic analysis report that includes a timeline, cost, and, in some cases, a sample recovery. If the analysis fails or your data cannot be fully recovered, you will be notified via email, and there will be no charge or a refund of the analysis fee. 
09
I only want to recover a few files or a single small file. What is the cost for partial recovery?
The cost of recovering data locked by ransomware like STOP/DJVU can vary based on several key factors, including:
• Degree of Data Header Damage: The more severe the damage caused by ransomware encryption, the higher the recovery cost.
• Complexity of Ransomware Encryption: Ransomware types such as elbie, makop, mallox, and lockbit utilize advanced RSA AES encryption, necessitating more resources for decryption.
• Type of Data to Be Recovered: Attacks on virtual machines and databases often involve complex encryption, increasing recovery costs. In some cases, ransomware employs multiple encryption IDs across different VMs, requiring separate decryption processes for each.
Estimated costs are also influenced by the dollar exchange rate, as payments for IBM-Q Quantum computing resources are made in USD. The three variables above determine the specifications of the Cloud Quantum computer used to reverse-engineer ransomware with the Shor algorithm.